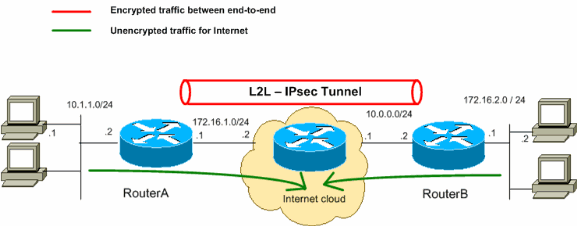
VIRTUAL PRIVATE NETWORKS
SyntonicMedia’s Virtual Private Network services provide safe secure communication for private data traveling across the public Internet. Through encryption, user and packet authentication, and access control, your network’s privacy is assured. You save money without having the investment in equipment, facilities, and in-house security expertise necessary to manage security on your Internet network. SyntonicMedia uses Check Point’s family of VPN encryption products to provide VPN solutions for intranets, extranets, and remote access applications.
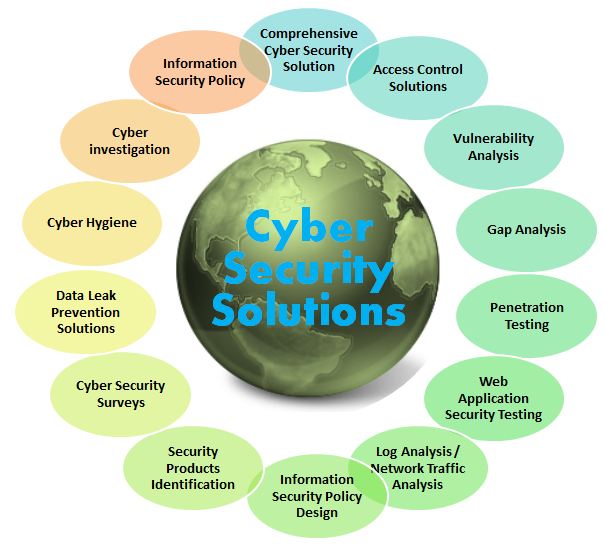
SECURITY SOLUTIONS
When you lack the internal resources to meet the demands of enterprise security management, a partner in information security consulting can fill the gaps.
Information security has become an incredibly complex effort. The threat landscape is growing and evolving quickly and new technologies for defense and controls emerge almost daily. It’s no longer enough to protect the network – effective IT security must involve security for data, endpoints, and web application security as well. Building a successful security program today requires extremely talented professionals who can develop a cyber security strategy and sort through all the options to choose the right mix of services, technology and solutions to build an effective program.
The right information security consulting partner can help you better protect your organization by providing expertise and experience that you may lack internally. When seeking an information security consulting company with the broadest experience and deepest expertise, more leading organizations today turn to Optiv.
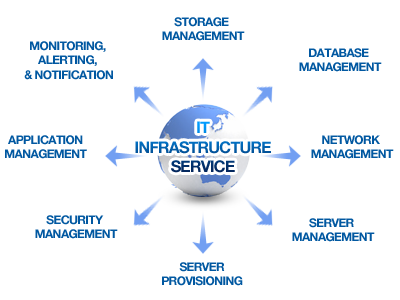
INFRASTRUCTURE TRANSFORMATION
Information Technology (IT) has outgrown its role as a back-office cost center. Business leaders today are increasingly looking to IT to support technology-enabled business strategies. Our Technology Infrastructure Transformation practice can help change the way companies run their technology infrastructure organizations. We help our clients gain increased agility and scalability, lower risk, and improve service quality.
Delivering effective technology infrastructure
Many leaders understand that yesterday’s technology infrastructure cannot withstand tomorrow’s competitive demands. They need an agile technology foundation. One that’s able to adapt to new products and business models. Scale up or down to meet demand. Harness greater computing power. Improve reliability and performance. Stand up to cyber threats and regulatory scrutiny. And more. Fulfilling these expectations requires more than technical know-how; effective technology leaders must also develop a business mindset.
How we can help
Contemporary CIOs, CTOs and COOs are taking a new approach by running their technology infrastructure as if it were a standalone business. They invest in infrastructure just like they would any business—expecting it to deliver products and services with the transparency and quality that they’ve come to expect from providers. Helping organizations achieve this shift is where Deloitte leads.
Our Technology Infrastructure Transformation practice brings together a global network of professionals with deep experience across technology, strategy, risk, financial advisory, tax, and human capital to help transform the way our clients run their technology infrastructure organizations.
Our services
We help our clients gain increased agility, lower risk, greater scalability, and improved service quality across: